As Far As Possible: United States Lab's Polylithic Enumerated Function Registry
Interoperation, Sequencing, and Mechanisms for a Secure, Decentralized, Scalable, and Constitutional Compound Republic
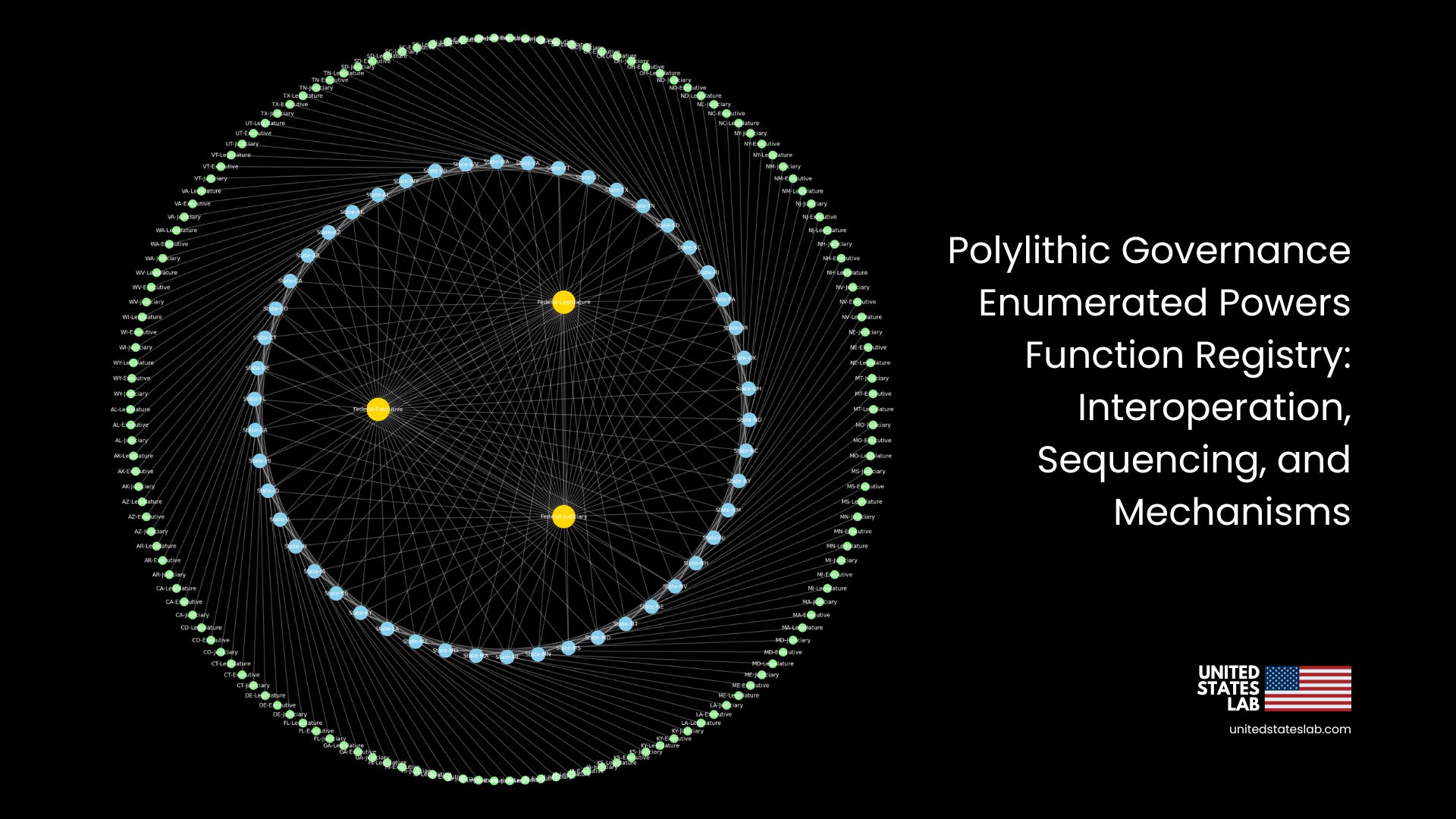
This article sets out in technical detail how every enumerated function of the United States Government can operate as an executable module inside United States Lab’s Polylithic Governance architecture, a system expressly designed to carry forward James Madison’s charge to “watch, to cherish, and as far as possible to perfect” the constitutional experiment. In this model, the legislative, executive, and judicial departments are specialized validator sets within a coordinated constitutional network. The states function as federated replicas, each preserving its independent authority while contributing to a shared, verifiable governance ledger.
At the heart of the system, the President serves as the execution-layer guardian, ensuring that no action advances to finality without passing the constitutional validity checks that Madison intended. Every enumerated power, whether to raise armies, regulate commerce, coin money, or amend the Constitution, is expressed as a precisely defined execution function, tied to its constitutional clause, constrained by governance primitives, and enforced through cryptographic proofs.
The architecture translates these functions into blockchain-style execution semantics—state insertions and mutations, ledger appends, deterministic state trie updates, and formally verifiable proofs, all synchronized through challenge periods and epoch-based renewals. In this way, United States Lab operationalizes the Madisonian system in code, providing a path to restore and perfect the balance of powers, the security of rights, and the stability of the Union—as far as possible—for generations to come.
Architectural Overview
Validator Sets (Core roles)
Legislature (House + Senate) — Bicameral validator set with distinct membership, quorum rules, origination rules, and supermajority thresholds. Output: legislative artifact (bill/resolution) suitable for presentment.
Executive (President + Departments) — Execution engine and guardian of the constitutional protocol. Output: execution signatures, promulgation, administration, command authorities.
Judiciary (Supreme Court + Inferior Tribunals) — Adjudication & Reversibility layer, providing post-facto validation, rollback/remedy, and conflict resolution.
Federated Layer (States) — Parallel validator sets that perform ratifications, elections, licensing, and interposition-style challenges where applicable.
USL Governance Primitives (Constraint Fabric)
Bicameral Filtering • Veto Mechanisms • Impeachment & Removal • Statute Limits & Delays • Adjudication & Reversibility • Juror Pools / Citizen Sortition • Threshold Voting • Proxy & Delegation • Challenge Periods • Separation of Powers • Citizen Challenge • Epoch Renewal • ZK Participation / Privacy Shielding
Execution Semantics (Blockchain)
Operation Types: State Insert • State Mutation • Ledger Append • State Query • Access Revocation (deprecate) • Action Dispatch • Consensus Verification • Quorum Ratify
State Trie Layers: Storage Root (global parameters, finance, war posture) • Contract Storage (programmatic authorities, registries) • Logs (events, attestations) • Calldata (messages, reports) • ZK Shielded State (privacy-preserving tallies and credentials)
Proofs: Signatures • Inclusion proofs • ZK proofs (SNARK) • Challenge/response • Validator multisig
Guardian Model
The President applies Exec Signature Required gates:
Yes (Veto or Execute) for legislative outputs;
Yes (Execute with Consent) for treaties and appointments;
Yes (Veto Overridden) on supermajority override.
This models presentment as a final validity check before execution.
Global Sequencing Model
Legislative Path (Statute Lifecycle)
Origination — Initiated under House/Senate procedural rules; revenue bills originate in the House. Drafting occurs in committees with amendments, public hearings, and markup sessions before being scheduled on the floor agenda.
Chamber Vote (Threshold Voting) — Each chamber applies quorum checks and its defined voting threshold (simple majority, supermajority for certain measures) with roll-call proofs. Vote outputs are cryptographically attested.
Bicameral Filtering — Both chambers reconcile differences through conference committee negotiations; a final identical text is produced and passed in each chamber, forming a dual-signed legislative artifact.
Presentment to Executive (Separation of Powers) — The finalized bill is formally transmitted to the President, acting as the guardian validator.
Guardian Decision:
Sign → Promulgation: Ledger Append of statute metadata; State Insert/Mutation in the state trie for new authorities, code paths, and appropriations; event log for execution readiness.
Veto → Return with formal reasons; Congress may attempt an override (2/3 both chambers) proven by supermajority quorum attestations; on success, statute proceeds to promulgation.
No action (timers): If the President takes no action within the constitutional window, apply either pocket veto rules or automatic promulgation, depending on adjournment status.
Publication & Codification — Commit canonical text hash to immutable storage; publish event logs to downstream executors, agencies, and public archives.
Execution — Agencies perform Action Dispatch under appropriations and authorities; execution proofs and status logs are generated.
Challenge Periods — Timed windows allow citizens, states, or authorized actors to submit constitutional challenges; courts invoke Adjudication & Reversibility protocols.
Statute Limits & Delays — Built-in sunsets, delayed effective dates, and staged rollouts managed through epoch gates; periodic Epoch Renewal events trigger reauthorization or deactivation.
Treaty Path
Executive Negotiation — Initiated by the President or delegated envoys; involves bilateral or multilateral talks, drafting treaty text, and establishing provisional terms. Negotiation metadata and draft hashes are logged for provenance.
Senate Advice & Consent — The finalized treaty is submitted to the Senate; Threshold Voting applies (often 2/3 majority). Debate and committee review occur before the final roll-call vote, with quorum proofs and public ledger attestation.
Executive Execution — Upon consent, the Exec Signature Required is satisfied. The President signs the instrument, triggers promulgation, and coordinates with Congress for any enabling legislation required. Treaty commitments are appended to the Storage Root, and implementation orders are dispatched to relevant agencies.
Appointment Path
Executive Nomination — The President selects a candidate, transmits the nomination with background dossier to the Senate.
Senate Consent — Hearings, committee vetting, and final vote (majority or higher threshold as per role). Vote outputs are recorded with quorum verification.
Commissioning and Oath — Upon consent, the President issues a commission. The appointee swears the constitutional oath; role activation is written to Contract Storage; event logs capture credential issuance.
Impeachment & Removal — For misconduct, the House issues articles of impeachment; the Senate conducts a trial, with conviction triggering removal. Removal events update role status in registry and log the change.
Amendment Path (Federated)
Propose — Amendments may originate in Congress (2/3 vote of both chambers) or via a convention called by 2/3 of state legislatures. Proposal text hashes and provenance proofs are recorded.
Ratify — Approval by 3/4 of state legislatures or conventions. State validator sets log Quorum Ratify events; ZK proofs may shield individual state votes while verifying aggregate tallies.
Publication — Upon ratification, the constitutional parameter set is updated in the Storage Root; public ledger entry finalizes the change.
Adjudication Path
Filing — Litigants submit case filings; docket metadata and jurisdiction claims are logged.
Original/Appellate Jurisdiction — Routing based on constitutional and statutory rules; proofs of jurisdiction validity are attached.
Hearing — Oral arguments and evidence presentation; proceedings are recorded in logs.
Opinion and Judgment — Court issues written opinion; judgment state changes recorded. Reversibility events write corrective transitions to affected state.
Precedent — Opinion references constitutional clauses and prior decisions; binding precedent entries are stored in Logs for future interpretive use.
Function Families — Mechanisms, State Effects, Timing
Legislative: Fiscal & Economic
levyAndCollectTaxes — State Insert (rates, bases, collection parameters) at Storage Root; logs for schedule and remittance. Timers for effective dates and fiscal-year epochs.
borrowOnNationalCredit — State Insert of debt ceilings/issuance programs; inclusion proofs for issuance; interest schedules as epoch series.
standardizeMonetarySystem — State Mutation of currency/valuation parameters; guardrails: Separation of Powers + Citizen Challenge window for unlawful delegation.
prosecuteCurrencyForgery — criminalization authority; Action Dispatch to DOJ; logs of prosecutions (privacy-preserving case metadata where required).
enactMeasurementStandards — State Insert of canonical unit registry; immutable reference hash published.
Legislative: Infrastructure & Knowledge
buildPostalNetwork — Establishes, maintains, and expands a national communications and logistics backbone; contracts and appropriations fund infrastructure; agency execution emits Logs recording route topology, service schedules, and compliance with statutory service obligations.
protectInventorProperty — secureInnovationRights: Operates a patent and copyright registry granting time‑limited exclusivity; Contract Storage records intellectual property grants with automatic expiry and renewal rules (Epoch Renewal) to incentivize innovation while eventually returning rights to the public domain.
createFederalCourts — State Insert defining the number, type, and jurisdictional scope of federal tribunals; seat counts and geographic districts stored as parameters; activation requires appropriation events and judicial appointment flows.
prosecuteMaritimeAndForeignCrimes — Enumerates extraterritorial offenses and prescribes jurisdiction; Action Dispatch to DOJ/Navy investigative units; prosecutions bound to constitutional venue and due process requirements.
Legislative: Defense & Militia
authorizeWarDeclaration — Ledger Append updating the war posture flag in Storage Root, which reconfigures execution rulesets for military and fiscal powers.
raiseArmy • maintainNavy — Define authorized end strength, fleet composition, and appropriations; parameters stored at Contract Storage level and updated by appropriation acts.
regulateArmedForces — Codify the Uniform Code of Military Justice, rules of engagement, and oversight protocols; updates mutate standing orders and operational parameters.
activateMilitia • organizeMilitia — Specify call‑up criteria, training standards, and equipment requirements; Federated readiness attestation proofs sync national and state militia registries.
Executive: Guardian & Operator
executeFederalLaw — Orchestrates agencies to carry out statutory mandates; validates statute hash against canonical promulgated version before dispatching execution orders.
commandMilitary — Issues operational directives (Action Dispatch) under active war posture or defensive authorities.
consultCabinet — Collects policy input and situational reports (Calldata) from department heads and principal officers; archives for provenance.
grantClemency — State Mutation altering sentence state (commutation, pardon) in the judicial enforcement record.
formTreaties — Conducts negotiations, produces signed instruments, and submits for Senate consent; upon approval, commits treaty obligations to Storage Root.
appointFederalOfficials • fillVacantOffices • commissionOfficers — Activates role credentials in Contract Storage; event logs capture commission details, oath records, and credential validity.
reportStateOfUnion — Ledger Append entry detailing national condition, priorities, and legislative agenda; timestamped and hashed for public and congressional record.
recommendPolicy — Signals proposals or preferred legislative directions; logged to inform congressional action.
summonCongress • resolveCongressDispute — Calls special sessions, sets adjournment dates, or resolves inter‑chamber disputes per constitutional provisions.
vetoLegislation — Exercises Veto Mechanism by returning unsigned legislation with objections; triggers override path if Congress musters supermajority.
Judiciary: Adjudication & Reversibility
interpretLaw • reviewConstitutionality — Issues binding opinions interpreting statutes and constitutional provisions; updates interpretive state used by all branches.
resolveStateOrFederalDisputes — Hears and decides conflicts between states or between states and the federal government; judgments recorded in Logs and applied to Contract Storage parameters.
guaranteeJuryTrial — Ensures procedural guarantees for jury trials in criminal cases; maintains procedural standards registry.
hearOriginalCases • reviewLowerCourtDecisions — Routes cases per jurisdictional rules; appellate decisions may reverse or affirm lower rulings, updating relevant state.
Federated: Cross-Replica Governance
proposeAmendments • ratifyAmendments — Initiates amendment process via congressional supermajority or convention; records proposals and state ratifications as Quorum Ratify events with proofs.
administerElections — Manages elections using ZK Shielded State for secret ballot integrity; publishes aggregate tallies with inclusion proofs.
grantCivicLicenses • charterLocalGovernments — Operates registries for licenses and charters within state scope; updates recorded in Contract Storage.
governInStateCommerce — Enacts and enforces intrastate economic regulations.
assertStateNullification — Allows states to formally challenge federal action; challenge records and proofs lodged for adjudication.
Multisig & Signatures — Who Signs What
Legislative artifacts: Yes (Bicameral Quorum) — Both House and Senate validator sets must sign, each meeting their quorum and voting thresholds. The dual-signature artifact is hashed and logged as a single canonical bill ready for presentment.
Executive actions: No (Single Actor) — The President’s signature alone advances most executive functions, except when Senate Consent is constitutionally mandated (i.e., treaties, appointments). In those cases, the Senate validator set’s signature is appended before execution.
Overrides & Impeachment: Yes (Supermajority / House+Senate) — Requires recorded supermajority attestations from both chambers, cryptographically bound to the override or conviction event.
Amendments: Yes (Federated Ratification) — State-level validator sets individually sign ratification events; these are aggregated into a 3/4 supermajority proof before the Storage Root is updated.
Challenge, Rollback, and Safety
Challenge Periods — Defined time windows post‑execution, analogous to the fraud‑proof window in optimistic rollups, during which eligible actors (citizens, states, oversight bodies) may submit constraint violation proofs. The transaction is treated as provisionally valid until the challenge window closes without a successful proof.
Adjudication & Reversibility — Functions as the dispute resolution layer: the Judiciary, acting as the on‑chain verifier, can review, suspend, or roll back actions. Rollbacks mutate state to prior valid checkpoints by applying corrective state transitions rather than deleting history, ensuring full immutability while restoring constitutional compliance.
Juror Pools / Citizen Sortition — Operates like decentralized fraud‑proof committees: randomized or criteria‑based selection of citizen validators to review challenges, simulating an off‑chain arbitration panel that returns a validity or invalidity verdict. Their decision becomes a signed proof affecting state.
Statute Limits & Delays — Acts as time‑lock contracts and self‑destruct conditions for governance actions: automatic expiration, delayed activation, and phased rollouts are enforced through state parameters and epoch timers, ensuring the system can only progress to the next state if predefined constitutional timing constraints are met.
Timing & Epochs
Legislative Session Epochs — Define start/end blocks for bill introduction and passage, synced to fixed-length governance epochs so that statute consideration windows align with representative terms. These epochs can be parameterized to auto-close agenda items when legislative authority refreshes at the next election.
Budget Epochs — Annual or multi‑year fiscal cycles controlling appropriation availability and reporting deadlines. Budgets are bound to legislative terms, ensuring that appropriations and fiscal authorizations do not outlive the validators who enacted them.
Election Epochs — Regularly scheduled intervals for citizen validator renewal, credential issuance, and reset of delegation weights. Citizen stake delegation to representatives is re‑affirmed or re‑allocated at these epochs, updating quorum calculations and validator set composition for the next term.
Judicial Epochs — Terms and review cycles for courts to reassess precedent or revisit standing orders, often aligned with staggered term completions of judicial offices. Judicial epoch boundaries trigger re‑attestation of court rosters and re‑anchoring of interpretive state into the Storage Root.
Interfaces & Data Contracts
Inputs — Highly structured governance payloads formatted to schema: proposal data (bills with section hashes and amendment diffs), nominations (with credential proofs and background attestations), treaty texts (content‑addressable CIDs with negotiation provenance), or case filings (with jurisdictional claims and procedural metadata). These payloads are versioned and content‑hashed for immutability.
Guards — Layered enforcement predicates that run prior to any state change: constitutional clause compliance checks, quorum proofs via Merkle‑rooted roll‑call trees, multisig threshold verification for validator sets, and conflict‑of‑interest screens that reference disclosure registries to disqualify conflicted signers.
Effects — Deterministic and scoped mutations to the governance state trie: updates to the Storage Root for global parameters, ledger appends for statutory or treaty enactments, contract storage key/value updates for program registries, and emission of structured event logs to subscriber processes for downstream execution.
Proof Outputs — Comprehensive cryptographic artifact bundles proving valid process execution: aggregated BLS or threshold ECDSA signatures from required validator sets, inclusion proofs demonstrating payload presence in authorized Merkle tries, and optional zero‑knowledge attestations for shielded operations (i.e., secret ballots, sealed deliberations). These proofs are stored on‑chain and can be independently verified by any node in the federated USL network.
Interoperation Technical Summary
The USL architecture models interoperation as a strict, cryptographically verifiable handshake between branches, enforced through:
Primitives-as-Guards — Constitutional constraints implemented as executable predicates.
Proof Bundles — Multisignature attestations, quorum proofs, and optional zero-knowledge proofs.
Deterministic State Trie Mutation — Scoped writes to branch-specific trie segments anchored to a global Storage Root.
Artifact Types
Every cross-branch action produces a standardized artifact:
Legislative Artifact —
{ billHash, textCID, quorumProofs[], bicameralProof }Presentment Envelope —
{ billHash, bicameralProof, deadline, clerkSig }Executive Decision Record —
{ billHash, decision, execSig, timestamp }Override Packet —
{ billHash, houseProof, senateProof, overrideSig }Treaty Instrument —
{ treatyID, textCID, execSig }Senate Consent Bundle —
{ treatyID, consentProof, senateSig }Appointment Bundle —
{ nomineeID, officeID, execSig, consentSig }Judgment Record —
{ caseID, holdingCID, courtSig, mandateSpec }Federated Ratification Packet —
{ amendmentID, stateProofs[], aggProof }
Artifacts reference off-chain text via content-addressable hashes (i.e., IPFS CIDs) and are idempotent — replays are no-ops.
Guard Execution Layer
Guards enforce prerequisites:
QuorumGuard — Confirms quorum and threshold per chamber.
BicameralGuard — Confirms identical billHash passed both chambers.
PresentmentGuard — Ensures delivery within constitutional window.
ExecGuard — Verifies executive authority signature.
ConsentGuard — Verifies Senate consent threshold for specific powers.
OverrideGuard — Confirms 2/3 supermajority in both chambers.
FederatedGuard — Aggregates state-level ratification proofs.
ConflictGuard — Prevents state changes conflicting with constitutional parameters or judicial mandates.
Proof Bundles
Each transaction includes a proofBundle containing:
Signature sets — Aggregated via BLS or threshold ECDSA, with signer indices tied to validator registries. Signatures are sorted, deduplicated, and packed into a canonical format to guarantee deterministic verification results across replicas.
Quorum attestations — Generated as Merkle roots of member roll calls. Each leaf node is a
{memberID, vote, signature}tuple; branch nodes are hash concatenations, and the root is committed alongside the action hash.ZK proofs — For shielded processes like secret ballots. These are SNARK-based, verifying constraints such as eligibility and tally correctness without revealing individual votes.
Cross-branch commitment proofs — Bind an artifact from one branch to acceptance in another by committing the artifact hash into both branches’ trie segments.
State Trie Propagation
USL uses a deterministic state trie mutation model similar to Ethereum’s Merkle Patricia Trie, but specialized for governance operations.
Authoritative Segmentation — Each branch and federated replica owns a disjoint namespace in the global trie. Keys are prefixed with a branch/replica identifier, ensuring that a write can never collide across governance domains.
Scoped Writes — Functions can only mutate keys within their scope. For example,
levyAndCollectTaxescan mutateStorageRoot.fiscalState.taxRatesbut cannot touchdefenseStateortreatyRegistry.Mutation Process:
Guard checks pass.
Proof bundle verified.
Transaction payload decoded into a deterministic key-value mutation set.
Keys updated in the in-memory trie in lexicographical order (to ensure deterministic hashing).
New branch root computed and committed.
Global
StorageRootupdated by recomputing the Merkle root from all branch roots.
Consensus Checkpointing — After each mutation batch, a finalized checkpoint is created, signed by the validator set, and broadcast to all replicas.
Finality and Immutability — Because USL models constitutional processes, once a checkpoint is finalized it is immutable. Any judicial reversal writes a corrective mutation at a new key version, never overwriting the original.
This ensures that state convergence across all replicas is cryptographically guaranteed, and that each constitutional function is both provable and auditable down to the key-value change in the trie.
Sequencing
Pre‑conditions (applied before step 1): artifact canonicalization; content‑addressed text (CIDs); anti‑replay (sessionEpoch, nonce, issuerKeyEpoch); input schema validation.
Step 0 — Intake & Dedup
Queue artifact by domain (Legislative/Executive/Judicial/Federated) and priority (deadlines first).
Drop replays: if
artifactHashalready finalized → no‑op; if pending → coalesce.
Step 1 — Guard validation (deterministic order)
SchemaGuard→ required fields, canonical hashing.MembershipGuard→ map signer IDs to seats using the Validator Registry snapshot at vote height.QuorumGuard/ThresholdGuard→ recompute quorum roots from roll‑call leaves; compare to provided roots.ScopeGuard→ ensure the function can only touch its allowed keyspace.TemporalGuard→ presentment / veto / override / ratification windows, tied to scheduler epochs.JurisdictionGuard(Judiciary only) → original/appellate routing.ConflictGuard→ check against active Judgment Records and constitutional parameters (Storage Root).
Step 2 — Proof verification
Signatures: verify BLS aggregate or threshold ECDSA with key‑epoch metadata; ensure each signer is eligible at the recorded height.
Quorum roots: verify Merkle proofs for sampled members; recompute root deterministically.
ZK proofs (optional): verify SNARKs for shielded predicates (i.e., eligibility, secret tallies) using circuit version IDs.
Cross‑branch commitments: ensure artifact hashes are committed in both producer and consumer domains when required.
Step 3 — Deterministic state trie mutation
Compute the mutation set from the validated payload (fully normalized key paths and values).
Sort keys lexicographically; apply CAS (compare‑and‑swap) on versioned entries to prevent lost updates.
Commit as a single atomic batch to the branch sub‑trie; recompute branch root → recompute global Storage Root.
Persist a write journal (key, oldValueHash, newValueHash, version) for audit and possible reversal patches.
Step 4 — Event emission (outbox pattern)
Emit typed events (i.e.,
Presented,ExecutiveDecision,TreatyPromulgated,JudgmentEntered) with inclusion proofs.Deliver to subscribers (agencies, states, public mirrors) with at‑least‑once semantics; consumers must be idempotent on
artifactHash.
Step 5 — Finalization & Scheduling
Register or cancel timers (presentment deadline, challenge window close, sunset) in the constitutional scheduler.
On finality, seal checkpoint with validator signatures; publish checkpoint digest.
Parallelism: Namespaces (branch/replica prefixes) allow concurrent execution. Global Storage Root recomputation reduces branch roots in a fixed order to preserve determinism.
Safety & Recovery
Reorg Safety
Only act on finalized checkpoints (i.e., BFT commit or LMD‑GHOST + finality gadget). Pending artifacts are visible but non‑binding.
If an exceptional reorg exceeds safety bounds, re‑validate artifacts against the new checkpoint; idempotent writes prevent duplication.
Key Rotation
EmergencyInhibit(keyID)freezes a compromised key; publish CRL (revocation list) with inclusion proof.New key attested by the appropriate validator set (oath/office for Executive; en banc order for Court; seated roster for Chambers).
Artifacts are content‑addressed, so past signatures remain valid; only pending artifacts tied to inhibited keys must be re‑attested.
Rollback (Judicial Reversibility)
Courts issue a Judgment Record (JR) containing
mandateSpec(what to unwind/modify) and basis (holding CID).Runtime applies a Reversibility patch: write new versions at affected keys; never delete historical values.
Causality fence: dependent writes after the invalidated act are queued for re‑evaluation against the new state; some may auto‑void, others require explicit re‑affirmation.
Conflict Resolution
Precedence lattice encoded as policy: Constitutional parameters > Judicial mandates (JR) > Treaties > Statutes > Regulations > Executive orders.
ConflictDetectorscans candidate mutations; if a lower‑tier write conflicts with a higher‑tier constraint, emitERR_CONFLICT_WITH_HIGHER_TIERand reject.Implement lex specialis and lex posterior where applicable: a more specific or later statute can supersede earlier general rules unless blocked by higher tier.
Optimistic Execution & Challenges
Post‑commit, each artifact opens a challenge window (fraud‑proof period). Until it closes, the write is provisionally valid.
Any eligible challenger can submit a constraint‑violation proof (minimal counter‑witness). If upheld, a JR is minted and a reversal patch is applied.
Citizen stake delegation can empower representatives or juror pools to file challenges on constituents’ behalf within term‑bounded epochs.
Disaster Recovery & Continuity
Geo‑replicated archives of checkpoints and event logs; deterministic replay can reconstruct any state from genesis + events.
Periodic offline snapshots with signed manifests; cold‑storage keys for emergency governance (i.e., quorum key to resume scheduler).
Observability
Proof explorer surfaces inclusion proofs, quorum roots, signer sets, and timer states.
SLA monitors for liveness (timer execution, queue depth) and safety (guard failure rates, challenge frequencies).
As Far As Possible
By encoding every constitutional function as a verifiable execution path, United States Lab’s Polylithic Governance Function Registry creates more than a technical model, it provides a durable, enforceable means of carrying forward the Madisonian experiment. Each validator set, each federated state replica, and each guardian action is bound to proofs, constraints, and timing windows that preserve the original structure of the Union while adapting it to a world where verification can be instantaneous and tamper-proof.
This approach expresses the U.S. Constitution in a form that can be measured, audited, and defended in real time. The same checks and balances that once relied on procedure, precedent, and honor are here reinforced by immutable ledgers, multisignature thresholds, and open challenge mechanisms. In doing so, the system builds a constitutional environment where both national strength and individual rights are secured against drift, circumvention, or overreach.
In this way, United States Lab serves the restorative work Madison urged:
“We owe it to ourselves and to the world, to watch, to cherish, and as far as possible to perfect a new modification of the powers of Government…” — James Madison to Andrew Bigelow, April 2, 1836
Madison’s call to “watch, to cherish, and as far as possible to perfect” the constitutional framework was not a demand for change for its own sake, but for the careful cultivation of its principles so that they might endure.
Enforcing the Constitution’s limits with modern verification strengthens federalism, sharpens separation of roles, and ties public action to the consent of the governed, pushing the constitutional experiment toward its intended form. United States Lab takes up that work in the digital era, preserving the original allocation of powers, strengthening the mechanisms of accountability, and enabling citizens and states alike to participate in safeguarding the Union, as far as possible.
At United States Lab, we are implementing the United States Constitution's compound republic governance model in web3. If you are interested in this research, please follow our R&D work.